From social engineering to profile hijacking, social media accounts face many potential attack vectors. Social media security isn’t something companies can take lightly, especially in regulated industries like healthcare and finance. A brand’s online presence—including that of its senior leadership—is deeply connected to its reputation. A breach can damage customers’ confidence and put company information at risk.
Cybersecurity threats are constantly evolving, so companies need to evaluate and adjust. In this article, we’ll cover social media security best practices to help you develop a security-first approach for your organization’s accounts.
What is social media security?
Social media security refers to the strategies, tools and best practices businesses and individuals use to mitigate risk and protect assets across social media platforms. This includes safeguarding sensitive information like customer data, employee details and confidential business information.
Common social media security threats include:
- Password theft
- Account impersonation
- Phishing and social engineering
- Data breaches
With the right privacy and security measures in place, organizations can lower the risk of these attacks and maintain a positive reputation.
The importance of social media security
Social media security goes beyond preventing account hacks and phishing attempts. It’s essential for protecting your brand’s reputation, employee and customer information, as well as ensuring compliance with evolving data protection laws (like GDPR and CCPA) and avoiding financial losses.
Think of it this way: Every employee, vendor and leader who touches your social media accounts plays a role in your overall security posture. Why? Because social media is inherently public. Any security breach can instantly damage your brand’s reputation through inappropriate posts, misinformation or scams visible to a wide audience. On top of that, the real-time nature of social means a malicious post can spread like wildfire, leaving little time to react.
And the stakes for brands are high. Not only can failing to follow data protection regulations lead to hefty fines, it can also lead to lost revenue due to damaged brand trust. According to a Q1 2024 Sprout Social Pulse Survey, 78% of consumers agree that, compared to a year ago, a brand’s social media presence now has a bigger impact on whether they trust that brand.
Top social media security risks and threats
Here are the most common social media cybersecurity risks, along with sample scenarios of how they might occur in an organization.
Password theft
Password theft involves stealing login credentials (username and password) to gain unauthorized access to a social media account. This can be done by stealing the login credentials of an employee or through a brute force attack.
Password theft can apply to the networks and any third party tools used to access and manage social media accounts.
Account impersonation
Account impersonation in social media security refers to the act of creating a fake account that mimics a legitimate individual, brand or organization.
Attackers use these fraudulent accounts to deceive others into believing they are interacting with the real entity. This can include impersonating executives, employees or entire businesses to scam customers, spread misinformation or damage a brand’s reputation.
Phishing
Phishing is a common cyberattack where cybercriminals impersonate trusted entities via email or social media to trick individuals into sharing sensitive information, like login credentials or financial details. These messages may look legitimate, but often contain links or attachments that lead to malicious websites or install malware—programs intentionally designed to harm a device, network or server.
Phishing is a serious security threat, as it can compromise accounts and systems, leading to privacy breaches and financial loss.
Malware
Malware is malicious software designed to harm a device, network or server. On social media, it can be spread through links, downloads or attachments shared on various platforms.
One wrong click can lead to malware being installed on a user’s device, potentially compromising sensitive data or allowing attackers to take control of the system.
Social engineering
Social engineering is a manipulation tactic used to trick people into giving up sensitive information, like login credentials or financial details. Instead of using technical hacking methods, social engineers rely on psychological tricks to exploit human nature.
For example, a scammer impersonating a customer or a partner might send a direct message (DM) that includes a link to a malicious website. Without proper training on social media security best practices, your team might click the link, assuming it’s legitimate.
Spam and bot accounts
Spam and bot accounts are automated accounts used to spread spam, malicious links and misinformation, polluting your feed and potentially harming your brand. They typically mimic real users and can be tricky to spot.
The real threat lies in their ability to distribute harmful content, launch phishing attacks and impersonate legitimate users or brands. This increases cybersecurity risks for both your social media team and your followers.
Privacy breaches
Privacy breaches occur when unauthorized individuals gain access to personal or sensitive information shared through social media platforms. This can include login credentials, private messages, financial details or proprietary business information.
Breaches often happen due to weak security practices, phishing attacks or vulnerabilities within social media networks and third-party platforms.
4 social media security best practices to know in 2025
Here are some social media security best practices you can follow to safeguard your brand, employees and customers:
1. Implement strong password practices
Strong passwords are foundational to your social media security. They’re your first line of defense against unauthorized access, protecting your social accounts and any third-party management tools. But while most people understand the dangers of weak or shared passwords, it’s easy to fall short in practice.
That’s why it’s crucial to choose tools with built-in security features like multi-factor authentication and single sign-on. These features combat “password fatigue” by making it easier to create and manage strong, unique passwords for each account. They also make it much harder for unauthorized users to gain access, even if a password is compromised.
Equally important is avoiding manual password sharing (like keeping passwords in a shared note). This practice makes it impossible to track who has access to which profiles, creating a major security vulnerability. If you can’t control access, you can’t ensure security.
2. Educate employees about social media security
Social media moves fast. This rapid evolution allows cybercriminals to innovate quickly, and unfortunately, exploit vulnerabilities on a large scale. But here’s the thing: Many employees may not be aware of the unique security risks that come with using social media for business.
That’s why it’s crucial to educate your team about the specific challenges of social media security. Here are a few key reasons it requires extra vigilance:
- Public nature: Social media platforms are inherently public, making it easier for attackers to gather information about your employees and target them with personalized attacks.
- Decentralization: Security on social media is a shared responsibility between platforms, users and businesses. This makes it more challenging to enforce consistent security practices across the board.
- Third-party apps and integrations: Many marketers connect their social media accounts to third-party apps and services, which can increase the risk of data breaches if those apps have weak security practices.
Empower your team to make smarter security decisions with up-to-date training that includes specific examples of social media threats. By illustrating how these risks can play out in realistic scenarios, you can help employees recognize and respond to potential attacks effectively.
3. Regularly review and update access permission settings for third-party applications
People change roles, leave organizations and projects evolve. To maintain strong social media security, it’s crucial to regularly review and update access permissions for all your social accounts and any third-party tools.
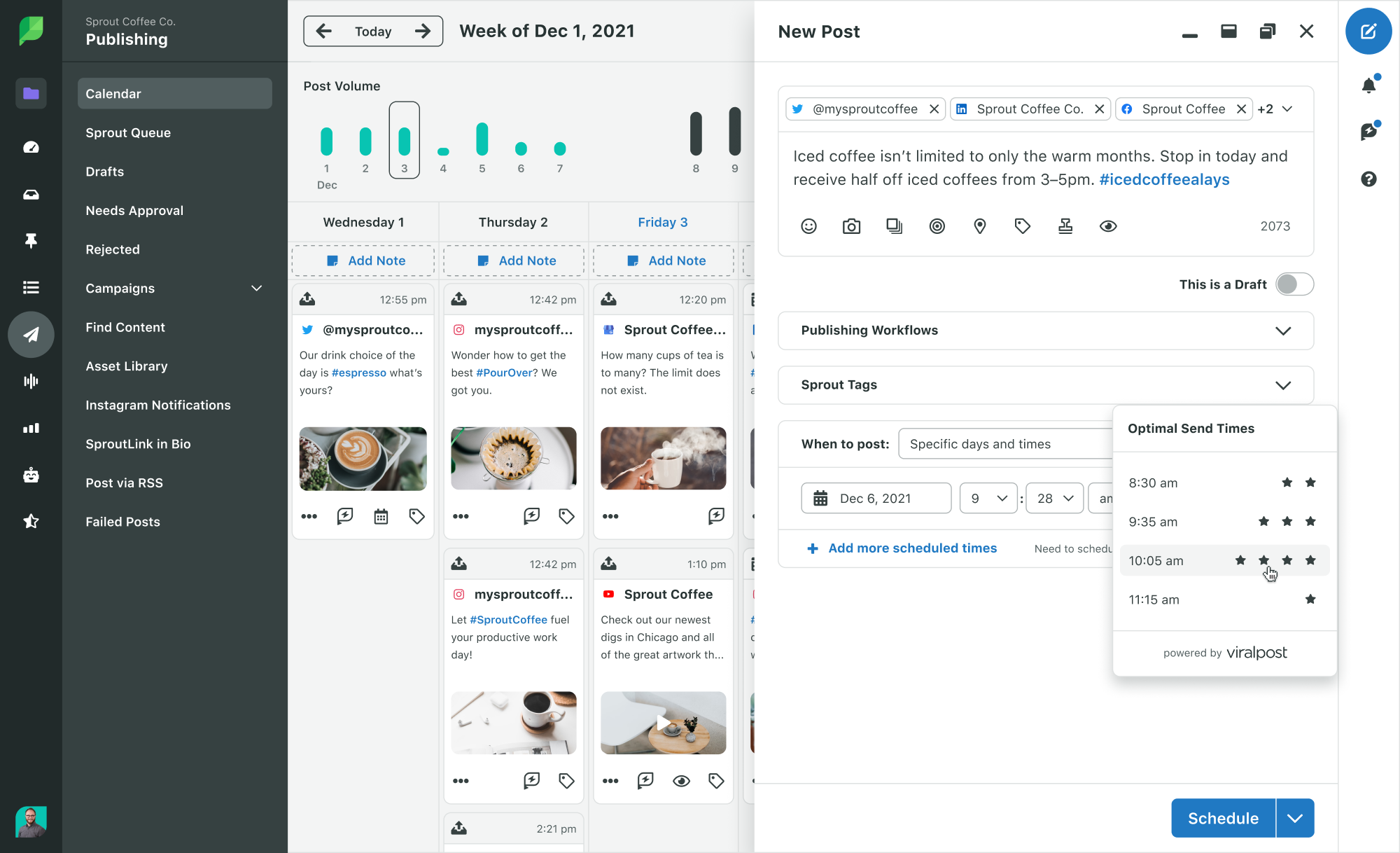
Start by setting clear user permissions. Your social media management platform should enable you to grant specific access levels based on each team member’s responsibilities. For example, in Sprout Social, you can set user permissions at the company and feature level. This ensures that team members have access to the tools they need—and nothing they don’t.
Equally important is establishing a clear workflow for removing system access when someone leaves the team or changes roles. This helps prevent former employees or those with new responsibilities from accessing sensitive information or performing actions they no longer have authorization for.
4. Create a social media crisis management plan
Crises don’t follow business hours. When a social media crisis hits, you need a plan to guide your response and minimize damage to your brand. This plan should outline the steps your team will take to address different scenarios, such as a hacked account or a data leak.
Imagine a hacker gains access to your social accounts and starts posting content that goes against your brand values. Or worse, what if they leak sensitive customer data? Without a plan, your response will likely be reactive, inconsistent and potentially damaging.
A strong social media crisis management plan will help you:
- Respond quickly and effectively to minimize damage.
- Communicate clearly and consistently with your audience.
- Protect your brand’s reputation and maintain customer trust.
- Coordinate efforts across different teams (social media, IT, communications, legal).
- Back up important data regularly and establish a recovery plan to handle security breaches.
- Learn from the experience and improve your future response.
Bonus Resource: Download our three-step template to document a social media crisis management plan. This template will help your team effectively respond and recover if a crisis strikes.
Social media security best practices for executives and brand advocates
Executives and fellow employees can be powerful brand advocates. Their personal social media posts can humanize your brand, build trust and reach new audiences. However, it’s crucial to ensure they can participate safely and effectively without compromising security.
Here’s how to empower these groups while maintaining a high level of social media security:
Executives
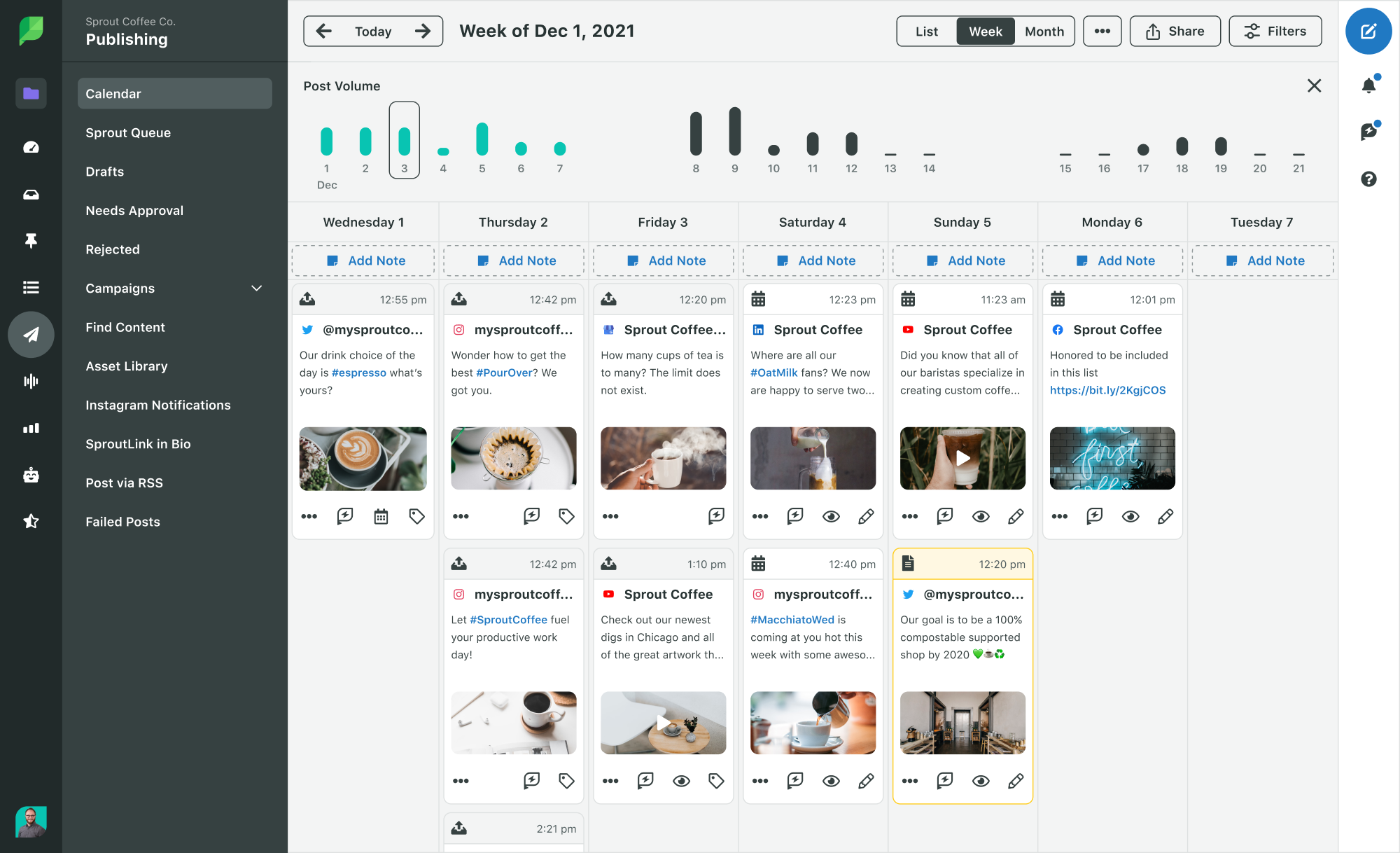
When it comes to executives, managing their social media presence within a secure platform is key. This eliminates the need for shared passwords and provides a centralized hub for managing content and approvals.
With Sprout Social, executive communications teams can efficiently oversee leadership profiles on LinkedIn and X (formerly Twitter). Easily schedule and approve posts, photos and videos directly within Sprout. If your executive prefers to approve content outside the platform, assign them an “External Approver Seat” to send content directly to their email for approval.
Employees
Employee advocacy is a powerful way to amplify your brand’s reach. Using a centralized platform enables employees to easily share pre-approved brand content while ensuring compliance with your company’s social media policy.
If your team has concerns about connecting their personal profiles to a company’s tool, reassure them that platforms like Sprout Social prioritize data privacy. Explain that Sprout only collects the essential information needed for employees to connect their profiles and share content from within the platform. This enables them to share company posts directly through our Employee Advocacy tool without needing to access their personal accounts.
How secure social media management tools keep you safe
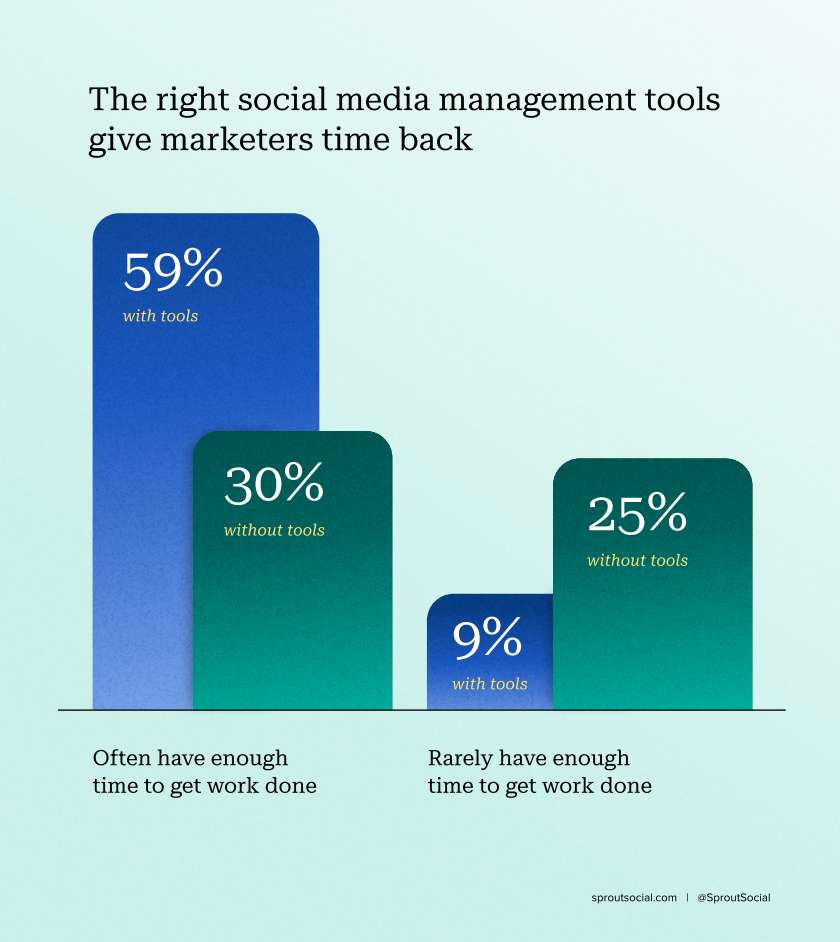
Secure social media management tools act as a central hub for all your social media activity, making it easier to control access, enforce security policies and monitor for suspicious behavior. They provide a layer of protection between your valuable brand accounts and potential threats, helping you mitigate risks and safeguard your reputation.
At Sprout Social, we understand the importance of keeping data secure. That’s why we’ve incorporated world-class, enterprise-grade security standards into our platform. We’re trusted by over 35,000 organizations to help them manage millions of daily conversations across social media.
Here’s how we prioritize security:
- Purpose-limited data processing: We clearly identify our purposes for processing personal data from social media networks and limit our processing solely to those purposes.
- Data minimization: We ensure that the personal data we process is adequate, relevant and limited to only what is necessary.
- Stringent data retention policies: We have established standard data retention periods for customer data and are stringent in ensuring that deletion requests are respected.
- Enhanced login security: We offer capabilities like single sign-on (SSO) and multi-factor authentication (MFA) to add extra layers of protection to user accounts and prevent unauthorized access.
- Responsible AI usage: We weave AI into our product responsibly to enhance our platform’s capabilities while prioritizing data security. Whether it’s Sprout’s proprietary AI models or integrations with third-party providers like OpenAI or Claude, Sprout never sells customer data and ensures these models cannot use or store data for model training.
For more on Sprout’s security and privacy standards, check out trust.sproutsocial.com.
Guarding the gateways to social accounts and data
Safeguarding your brand requires staying vigilant in the ever-changing cybersecurity landscape. Continually educate yourself and your team to stay ahead of emerging threats. Remain proactive, and you can keep your accounts secure today and into the future.
Managing all your accounts and permissions on one central platform is a significant step toward greater social media security. Request a personalized demo to discover how Sprout Social empowers over 35,000 brands to achieve smarter, faster business impact with comprehensive social media management solutions. Our platform includes tools for publishing, engagement, customer care, influencer marketing, advocacy and AI-powered business intelligence.
The post Social media security best practices to keep your company and customer data safe appeared first on Sprout Social.
from Sprout Social https://ift.tt/rPMAdFH
via IFTTT